For chief security officers (CSOs) and cloud IT teams or administrators, managing cloud computing security for a specific deployment can be arduous precisely because of the ease of use, flexibility, and configurability of cloud services. Cloud administrators must have a deep understanding of how their respective enterprises use the cloud, so that they can assign the appropriate security policies and standards, coupled with enforceable roles and accountabilities.
Traditional network-based security technologies and mechanisms cannot be easily or seamlessly migrated to the cloud. But security concerns faced by a network administrator remain mostly the same: How do I prevent unauthorized access to my network and avoid data breach? How can I ensure uptime? How do I encrypt communications or authenticate cloud players? How do I easily detect threats and spot vulnerabilities in developed applications?
Traditional network-based security technologies and mechanisms cannot be easily or seamlessly migrated to the cloud. But security concerns faced by a network administrator remain mostly the same: How do I prevent unauthorized access to my network and avoid data breach? How can I ensure uptime? How do I encrypt communications or authenticate cloud players? How do I easily detect threats and spot vulnerabilities in developed applications?
Understanding Shared Responsibility
Broadly speaking, the concepts of “security of the cloud” versus “security in the cloud” have been pioneered by Amazon to clarify the shared responsibility of vendors and customers with regard to cloud security and compliance. Vendors are mainly responsible for the physical and network infrastructure that make up the cloud service, and then a sliding scale is applied depending on the specific cloud service purchased, which then determines the customer’s direct security responsibility.
In more practical terms, as discussed in the Trend Micro article “The Cloud: What It Is and What It’s For,” the different cloud service models — infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service (SaaS) — determine which components — from the physical infrastructure hosting the cloud right down to the data created, processed, and stored in it — will be the responsibility of the vendor or the customer, and therefore who will be responsible for securing them.
In a PaaS deployment like Google App Engine, Microsoft Azure PaaS, or Amazon Web Services Lambda, for instance, developers can purchase the resources to create, test, and run software. Thus, as users, they are generally responsible for the applications and data while the vendor is bound to secure the container infrastructure and operating system — with, as previously mentioned, varying degrees of responsibility depending on the specific service acquired, which can differ in a more granular sense.
Security of the cloud is part of the offering of cloud providers. This is assured through contractual agreements and obligations, including service-level agreements (SLAs) with the vendor and the customer. Performance metrics like uptime or latency, along with expectations with regard to the resolution of problems that may arise, documented security capabilities, and perhaps even penalties for underperformance, can typically be managed by both parties through the setting of acceptable standards.
For the vast majority of cloud users, the rest of this primer discusses the challenges, threats, and other areas covered by “security in the cloud.”
In more practical terms, as discussed in the Trend Micro article “The Cloud: What It Is and What It’s For,” the different cloud service models — infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service (SaaS) — determine which components — from the physical infrastructure hosting the cloud right down to the data created, processed, and stored in it — will be the responsibility of the vendor or the customer, and therefore who will be responsible for securing them.
In a PaaS deployment like Google App Engine, Microsoft Azure PaaS, or Amazon Web Services Lambda, for instance, developers can purchase the resources to create, test, and run software. Thus, as users, they are generally responsible for the applications and data while the vendor is bound to secure the container infrastructure and operating system — with, as previously mentioned, varying degrees of responsibility depending on the specific service acquired, which can differ in a more granular sense.
Security of the cloud is part of the offering of cloud providers. This is assured through contractual agreements and obligations, including service-level agreements (SLAs) with the vendor and the customer. Performance metrics like uptime or latency, along with expectations with regard to the resolution of problems that may arise, documented security capabilities, and perhaps even penalties for underperformance, can typically be managed by both parties through the setting of acceptable standards.
For the vast majority of cloud users, the rest of this primer discusses the challenges, threats, and other areas covered by “security in the cloud.”

Figure 1. Security of the cloud versus security in the cloud
Main Challenges to Security
Enterprises may be migrating some requirements to the cloud, starting fully in the cloud (aka going “cloud native”), or mastering their mature cloud-based security strategy. Regardless of what stage a company is at along its cloud journey, cloud administrators should be able to conduct security operations such as performing vulnerability management, identifying important network events, carrying out incident response, and gathering and acting on threat intelligence — all while keeping many moving parts in compliance with relevant industry standards.
Managing Complexity
Cloud deployments do not have access to the same security infrastructure as on-premises networks. The heterogeneity of services in the cloud makes it hard to find cohesive security solutions. At any point in time, cloud administrators are supposed to be looking to secure a hybrid environment. The complexity lies in the reality that the risks in cloud computing vary depending on the specific cloud deployment strategy. This in turn relies on the specific needs of the cloud users and their risk appetite, or the level of risk that they are willing to take on. This is why risk assessment is an important exercise that cannot be simply lifted wholesale from published best practices or compliance. However, compliance guidelines serve as a baseline or framework that can be instrumental in raising the right questions with regard to risk.
Managing Complexity
Cloud deployments do not have access to the same security infrastructure as on-premises networks. The heterogeneity of services in the cloud makes it hard to find cohesive security solutions. At any point in time, cloud administrators are supposed to be looking to secure a hybrid environment. The complexity lies in the reality that the risks in cloud computing vary depending on the specific cloud deployment strategy. This in turn relies on the specific needs of the cloud users and their risk appetite, or the level of risk that they are willing to take on. This is why risk assessment is an important exercise that cannot be simply lifted wholesale from published best practices or compliance. However, compliance guidelines serve as a baseline or framework that can be instrumental in raising the right questions with regard to risk.
Gaining Visibility
As the speed of movement inside an organization is spurred by the ease of subscribing to cloud services, buyer decisions are suddenly no longer within the purview of the IT department. Yet the IT department remains accountable for the security of apps developed using the cloud. The challenge becomes how to ensure that, while movement and development remain efficient, IT can still view and secure every interaction in the cloud.
Security Risks and Threats in the Cloud
According to Trend Micro’s comprehensive review of the most common security pitfalls in cloud implementations, titled “Untangling the Web of Cloud Security Threats,” misconfigurations continue to be the most common weakness in cloud security among cloud users. This means that as cloud users set up their cloud instances or services, they tend to overlook important settings or change them unsecurely.
Threat actors can discover these misconfigurations and use them for various malicious activities, ranging from the highly targeted — involving cyberattacks conducted to target a particular organization either as an end goal or as a stepping stone to another network — to the more opportunistic. Apart from misconfigurations, threat actors can gain entry to cloud deployments via stolen credentials, malicious containers, and vulnerabilities in any of the layered software.
Actual attacks have resulted in organizations suffering losses, financially or otherwise.
Cloud-based attacks that can affect enterprises include:
— Cryptojacking, where threat actors steal an enterprise’s cloud computing processing power to conduct unauthorized cryptocurrency mining, which can hog resources and cause an increase in network traffic that will be charged to the enterprise
— E-skimming, where threat actors gain access to an enterprise’s web applications to inject malicious code that collects financial information from site visitors, possibly leading to large losses on the customer side that can then ultimately damage the company’s reputation
— Unauthorized access leading to data modification, breach, loss, or exfiltration, which can be done for a variety of threat actor end goals such as accessing customer detail databases to be sold in the cybercriminal underground or stealing trade secrets.
Threat actors can discover these misconfigurations and use them for various malicious activities, ranging from the highly targeted — involving cyberattacks conducted to target a particular organization either as an end goal or as a stepping stone to another network — to the more opportunistic. Apart from misconfigurations, threat actors can gain entry to cloud deployments via stolen credentials, malicious containers, and vulnerabilities in any of the layered software.
Actual attacks have resulted in organizations suffering losses, financially or otherwise.
Cloud-based attacks that can affect enterprises include:
— Cryptojacking, where threat actors steal an enterprise’s cloud computing processing power to conduct unauthorized cryptocurrency mining, which can hog resources and cause an increase in network traffic that will be charged to the enterprise
— E-skimming, where threat actors gain access to an enterprise’s web applications to inject malicious code that collects financial information from site visitors, possibly leading to large losses on the customer side that can then ultimately damage the company’s reputation
— Unauthorized access leading to data modification, breach, loss, or exfiltration, which can be done for a variety of threat actor end goals such as accessing customer detail databases to be sold in the cybercriminal underground or stealing trade secrets.
Areas to Secure in the Cloud
As cloud builders get into the specifics of their requirements from the cloud, they should take advantage of the opportunity to design their cloud deployments well enough for security to be built in at the beginning, so as to avoid the threats and risks discussed in the preceding section. By securing each of the following areas, where relevant, IT teams can navigate current and future cloud deployments confidently. These align with recommendations from Gartner's "Market Guide for Cloud Workload Protection Platforms" report for 2020.
Network (Traffic Inspection, Virtual Patching)
A critical piece of the security puzzle, network traffic inspection can be the line of defense against zero-day attacks and exploits of known vulnerabilities, and can provide protection via virtual patching. A firewall in the cloud is slightly different from a traditional firewall because the main execution challenge is being able to deploy the firewall in a way that does not disrupt network connections or existing applications, whether in a virtual private cloud or a cloud network.

Figure 2. Network security in the cloud must be able to “see” all of an enterprise’s traffic, regardless of its source.
Cloud Instance (Workload Security at Runtime)
Security language and paradigms change to accommodate the understanding of the components that need to be protected. In the cloud, the concept of workload is a unit of capability or amount of work that is done in a cloud instance. Protecting workloads against exploits, malware, and unauthorized changes is a challenge for cloud administrators, as they run in server, cloud, or container environments. Workloads are fired up as needed, dynamically, but each instance should both be visible to the cloud administrator and be governed by a security policy.
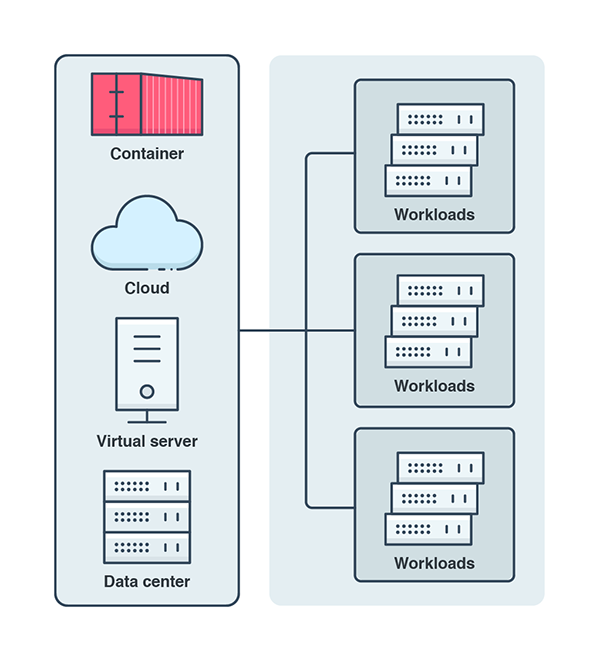
Figure 3. Workloads should be monitored for threats, regardless of their nature and origin.
DevOps (Container Security)
The software unit in cloud computing services has become centered on, at least in recent years, the container. Using containers ensures that software can run reliably well regardless of the actual computing environment, which can become complicated to replicate if, for instance, certain code, tools, system libraries, or even software versions need to be a certain way.
For developers and operations teams especially, integration of security during software development becomes even more relevant as cloud-first app development becomes more common. This means that containers must be scanned for malware, vulnerabilities (even in software dependencies), secrets or keys, and even compliance violations. The earlier these security checks are done during the build, preferably in the continuous-integration-and-continuous-deployment (CI/CD) workflow, the better.
For developers and operations teams especially, integration of security during software development becomes even more relevant as cloud-first app development becomes more common. This means that containers must be scanned for malware, vulnerabilities (even in software dependencies), secrets or keys, and even compliance violations. The earlier these security checks are done during the build, preferably in the continuous-integration-and-continuous-deployment (CI/CD) workflow, the better.
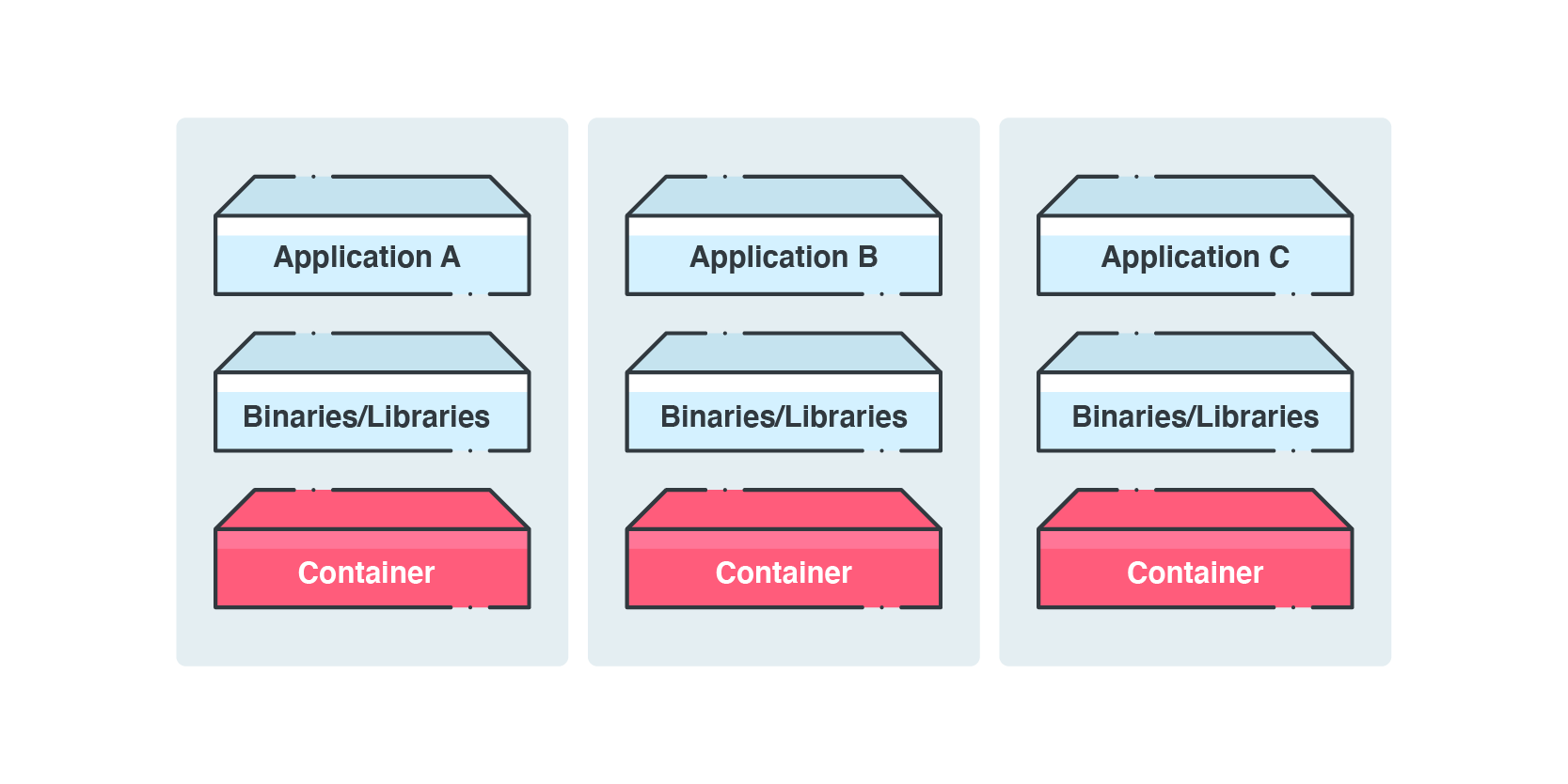
Figure 4. Containers are made up of different code stacks and components, and should be scanned for malware and vulnerabilities.
Applications (Serverless, APIs, Web Apps)
Traditional security cannot be deployed in certain serverless or container platforms, but applications themselves, however simple or complex, need to be secured as robustly as the other areas. For many companies, the fast and efficient programming and deployment of new applications are the primary drivers of going to the cloud. But these applications are potent entry points for web-application runtime threats like code injections, automated attacks, and remote command executions. If attacks do happen, details of the attacks must be accessible to cloud administrators.
File Storage
Companies look to the cloud, mainly or partly, as a way to offload storage from on-premises servers. Cloud storage for files or objects can be a source of infection if for any reason a known malicious file was uploaded to it. Scanning should be available for any kind of file, regardless of size, ideally before it is even saved to minimize the risk of other users accessing and executing a malicious file (if scanning is done after the fact).
Conformity and Governance
Data privacy regulations like the General Data Protection Regulation (GDPR), industry standards like the Payment Card Industry Data Security Standard (PCI-DSS), and pieces of legislation like the Health Insurance Portability and Accountability Act (HIPAA) have bottom-line implications for organizations capturing, processing, and saving data, especially in the cloud. Cloud administrators must balance these compliance requirements with the agility benefits of the cloud. Enterprises should be assured through security technologies that their deployments adhere to security best practices; if not, the fines that may arise from unknowingly committing violations can easily wipe out cost savings.
Cloud Security Technologies
With so many moving parts, an enterprise contemplating a cloud security strategy must look toward streamlining the necessary security technologies, from malware protection and intrusion prevention to vulnerability management and endpoint detection and response. The overall security solution must reduce the number of tools, dashboards, and window panes to be regularly used as basis for IT analysis. At the same time, it must be able to credibly visualize the abstract network boundaries of the enterprise’s entire cloud operations — whether an activity, such as on-the-fly tool development by one of the developers, was sanctioned by IT or not.
Trend Micro, for instance, can help DevOps teams build securely, ship fast, and run anywhere through the Trend MicroTM Hybrid Cloud Security solution. This solution provides powerful, streamlined, and automated security within the organization’s DevOps pipeline, and delivers multiple XGenTM threat defense techniques for protecting runtime physical, virtual, and cloud workloads. It is powered by the Cloud OneTM SaaS platform, which provides organizations a single-pane-of-glass look at their hybrid cloud environments and real-time security through its Network Security, Workload Security, Container Security, Application Security, File Storage Security, and Conformity services.
For organizations looking for runtime workload, container image, and file and object storage security as software, Deep SecurityTM and Deep Security Smart Check scan workloads and container images for malware and vulnerabilities at any interval in the development pipeline to prevent threats before workloads and container images are deployed.
Trend Micro, for instance, can help DevOps teams build securely, ship fast, and run anywhere through the Trend MicroTM Hybrid Cloud Security solution. This solution provides powerful, streamlined, and automated security within the organization’s DevOps pipeline, and delivers multiple XGenTM threat defense techniques for protecting runtime physical, virtual, and cloud workloads. It is powered by the Cloud OneTM SaaS platform, which provides organizations a single-pane-of-glass look at their hybrid cloud environments and real-time security through its Network Security, Workload Security, Container Security, Application Security, File Storage Security, and Conformity services.
For organizations looking for runtime workload, container image, and file and object storage security as software, Deep SecurityTM and Deep Security Smart Check scan workloads and container images for malware and vulnerabilities at any interval in the development pipeline to prevent threats before workloads and container images are deployed.
